Guide to Phishing Emails and How to Report Them
Introduction: What is a Phishing Email?
Phishing is a type of email scam that tricks people into revealing their personal information by pretending to be a trustworthy source in an email.
A phishing email is usually sent from an email address that looks somewhat similar to the one you might expect. It often appears to come from a legitimate company and asks for your personal information such as login credentials, Social Security number, banking info or money. The goal of the phishing email is to get you to click on links where they will ask you for specific information that will allow them to login to your legitimate account. Some emails try to get you to download and open attachments that can infect your computer with malware, steal your identity, or give hackers access to your bank account.
It’s important to NEVER open any attachments or click on any links in an unknown email, no matter how it looks. The only exception would be that you are expecting and attachment and it is from the source you are expecting it from.
How to Spot a Phishing Email
Below are some techniques that can be used to spot a phishing email:
- Watch out for typos.
- Be suspicious of links that take you to unfamiliar websites or those that don’t match the rest of the email.
- Look at the sender’s address carefully, and do not click on/open any attachments from senders you don’t know or trust.
- Look for grammatical errors, which can be an indication of poor English skills or a lack of attention to detail on the part of the sender.
- Do Not responding to emails from senders you don’t know, even if the email seems legitimate.
- Do Not open any attachment that you are not expecting, and don’t click on any links in the email.
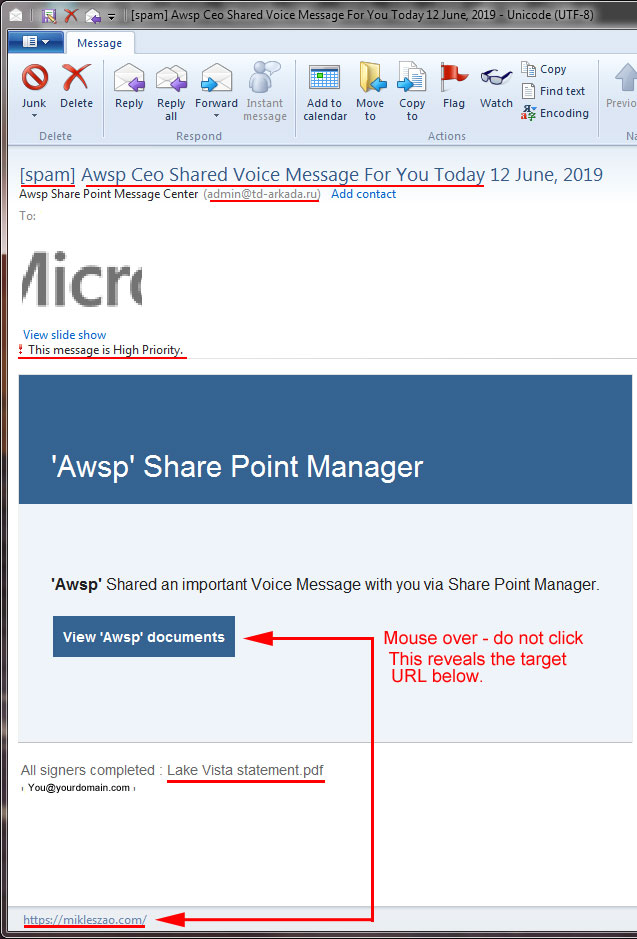
Marked as SPAM.
Does the subject make sense?
Senders email address – Russian
Marked high priority?
Mouse over the “View Document” to reveal destination URL.
Attachment make sense?
Identifying Red Flags
The key to identifying phishing, malware and scams is to simply use the power of observation. In the example to the left, I’ll show you what to look for.
Phishing emails typically try to personalize the message to try and convey trust by using your name, email address, business domain name and even company names and logos that you have done business with. They also try to impart a sense of urgency to act on your part. These tactics are all red flags.
First and foremost, what is the general look and feel of the email? Does it look professional or thrown together? Red flags can include a poorly designed email with spelling and grammatical errors.
In this example, scammers are trying to disguise this email as an inner-office email sent from share point. Let’s break it down.
#1) This is a poorly designed email AND It’s marked as SPAM. This is obvious but it is the first red flag. However, many phishing/scam emails you’ll receive won’t be marked as spam and can look almost look professional.
#2) Does the subject make sense? Are you expecting an email from this organization or person? Do you commonly receive voice messages from Share Point? Probably not. Let’s investigate further.
#3) Senders email address. Do you recognize the domain? Look at the extension, .ru is Russian. Shouldn’t have to go any further but lets proceed.
#4) Why would this be marked high priority? What evidence do we have so far? A poorly constructed email marked “SPAM” from a person or organization you don’t know, from a Russian email address. Hmmm. Not looking good.
#5) Mouse over the “View Document” or the “Take this Action” button but do not click it. The destination URL will be revealed in the lower-left corner of your mail client. Do you recognize this URL/Domain? No? Many times they will use a third-party URL shortener from another country.
#6) Does the subject of this fake PDF make any sense to you? No? Add all of this up and the email is a phishing or malware attempt.
It is safe to delete.
How long does this process take? Once you know what to look for, only a few seconds from review to delete.
How To Report A Phishing Attempt
There are several ways to report a phishing attempt. Taking the time to do this will benefit others and eliminate one source.
Submitting to Google
- To report the phishing website to Google, go to Google’s Report Phishing page
- In the email, right-click the link and select “Copy Link Address”
- Paste the link in the URL Field, give a short description and submit.
- Google Will review and flag the site.
Submitting to the FTC
- If you got a phishing email, forward it to the Anti-Phishing Working Group at [email protected]. If you got a phishing text message, forward it to SPAM (7726).
- Report the phishing attack to the FTC at ReportFraud.ftc.gov.
Submit to the US Government Cyber Security and Infrastructure Agency
https://www.cisa.gov/uscert/report-phishing
Conclusion: How To Protect Yourself From Phishing Emails
We are all aware of the dangers of phishing emails, however, many people still fall for them everyday and phishing has become a very profitable industry in and of itself.
This is why it is important to learn how to identify a phishing email. Once you know what to look for, you will never have to worry about getting scammed again.
The most important thing to remember about phishing emails is that they are designed to steal your personal information. The goal of the email is to impart a sense of urgency or to scare, startle, or alert you into clicking on a link quickly without thinking.
The number one rule is to never click on anything in the email or respond to the sender in any way.
Take your time and examine the email as outlined above. Nothing is so urgent that you must act immediately. If you are still unsure, contact your email support team and have them review it.


